Manage complex cryptographic environments from one location
Over time, an organization may have anything from hundreds to millions of keys being used within a complex cryptographic environment. SvKMS’s custom key import feature allows users to import keys that may have created by another key manager in a common format, or through a custom algorithm.
Integrate legacy encryption keys – including PGP, GPG, DES, CAST and Blowfish – into one centralized key manager, reducing complexity and administrative overhead.

Import unique and legacy custom keys
Manage both modern and legacy encryption keys with one single key manager.
Administer new and old encryption workflows
Consolidate and manage encryption workflows under one pane of glass.

Take advantage of modern key lifecycle management
Modernize your key management while maintaining legacy protocols.
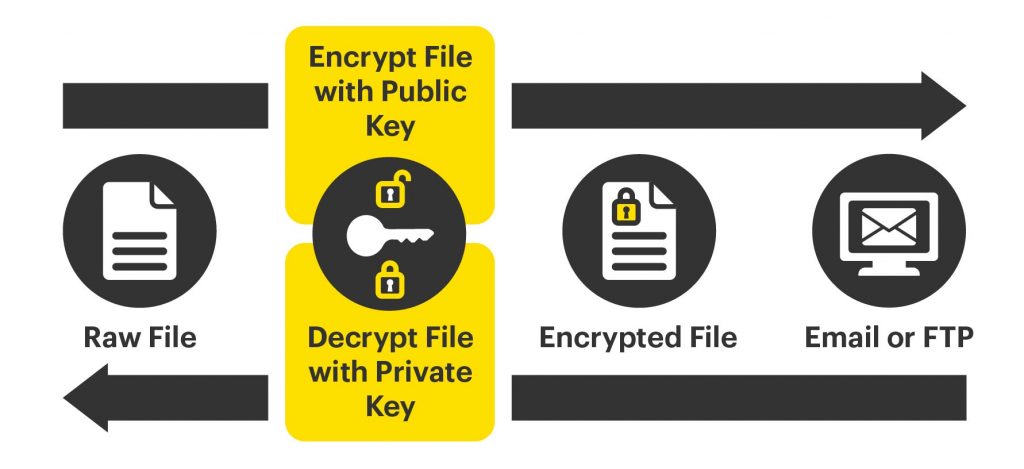
Integrate PGP encryption across your environment
Since it was first introduced in 1991, Pretty Good Privacy (PGP) has been used as an encryption method for text, email, directories and even disk partitions by using public and private key pairs for encrypting and decrypting data.
Many companies have been using PGP encryption for years, and managing these keys alongside more modern solutions for data encryption can be problematic, resulting in a fractured key management environment.
SvKMS can be used to centralize the management of these keys, allowing continued access to the data these keys protect, while at the same time providing an industry-leading KMS for all your new data encryption requirements.
Robust lifecycle management with SvKMS
Like so many other key management workflows, custom keys need to be properly managed to be secure. SvKMS provides full key lifecycle management and direct integrations into legacy encryption methods.
Extend HSM value by taking advantage of modern key management
Though long the gold standard of on-premises secure key storage and data encryption, it can be increasingly challenging to maximize hardware security module (HSM) value within the enterprise. Reduced relevance of HSMs in supporting important new workflows like cloud, SaaS and Edge make it a challenge to justify HSM cost.
SvKMS extends the reach of HSMs to include a multitude of new workflows and layer on new, integrated features like advanced key management capabilities and key-level security policies.
