What is Encryption?
Encryption is the process of information protection by transforming readable data, often referred to as plaintext, into an unreadable format known as ciphertext, using an algorithm and an encryption key.. If data falls into an unauthorized party’s hands, it cannot be read without having the correct encryption keys to decrypt the data. Only members of an organization that have access to the encryption key(s) can translate the files to make them readable.
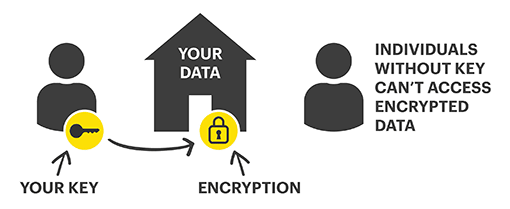
The concept of encryption could be compared to protecting your home from being accessed by strangers, with a lock and key. In this analogy, the “lock” equates to encryption, keeping unauthorized individuals from accessing your house (or your data). Your house “key” is the equivalent to an encryption key, which is used to lock and unlock the door to the house. Only individuals that possess the key can lock / unlock the front door to your house (or encrypt / decrypt your data). If the key falls into the wrong hands, someone that you don’t want entering your home could break in and steal your personal belongings. If a cybercriminal steals or manages to forge an encryption key, the ‘door’ is wide open for data compromise. Indeed, lock picking with enough time may also allow access to unauthorized entities. Remember, encryption of data does not guarantee its confidentiality, it is a way of making it harder to access. Hard enough to dissuade even thinking about breaking in.
How Does Encryption Work?
Using an algorithm that is based on a mathematical formula, encryption “scrambles” or encrypts an organization’s data, making it unreadable. When a user wants to unscramble the data, they then use a designated encryption key to decrypt the information. In its encrypted state, data is referred to as “ciphertext” and in its readable form it’s called “plaintext.”
To give you an idea of just how complex and advanced encryption algorithms are, it would take a normal computer around 300 trillion years to break an RSA-2048 bit encryption key , using what’s called a brute force attack. It’s the equivalent of trying every random key on a key ring, only in the digital domain this would mean trying any and all combinations of credentials, like usernames and passwords.
There are two different types of cryptographic algorithms – symmetric and asymmetric. A symmetric (private key) algorithm consists of a single key, that is only distributed amongst trusted members of an organization that are allowed access to sensitive data. These members use that key to both encrypt and decrypt information. An example of symmetric encryption is a password-protected PDF. The creator of the PDF secures the document using a passcode. Only authorized recipients that possess that passcode are able to view and read that PDF. In this instance, encrypting and decrypting are limited to individuals that possess the single key.
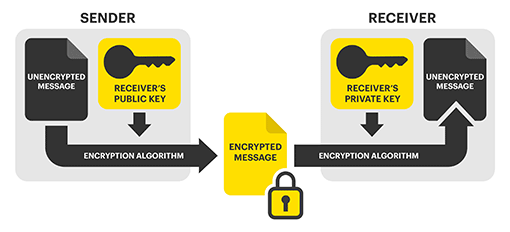
An asymmetric algorithm consists of two different keys – a private key and a public key. The private key is kept secret and only accessible by authorized users, while the public key can be shared freely. While the public key can be shared with anyone to encrypt plaintext, the private key is required to then decrypt that ciphertext. An example of asymmetric encryption would be sending out an email via a platform called Pretty Good Privacy (PGP). Anyone within an organization could use PGP to send out an encrypted email, using the recipient’s public key. However, only the recipient could decrypt and read the email, using their private decryption key.
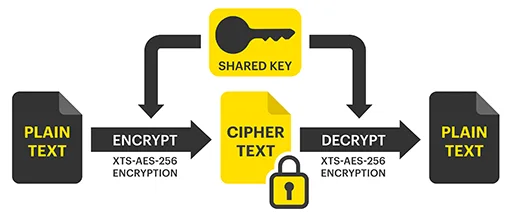
Symmetric key algorithm (above) and asymmetric key algorithm (below)
There are several common encryption algorithms that are widely used across various applications and industries. Here are some of them:
- AES (Advanced Encryption Standard): AES is a symmetric encryption algorithm widely adopted for securing sensitive data. It supports key sizes of 128, 192, and 256 bits and is commonly used in applications ranging from data encryption to network security.
- RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm used for key exchange, digital signatures, and public-key cryptography. It is frequently employed in securing communications over the internet, including SSL/TLS protocols.
- Diffie-Hellman Key Exchange: While not an encryption algorithm by itself, Diffie-Hellman is a key exchange protocol used to securely exchange cryptographic keys over untrusted networks. It is often combined with symmetric encryption for secure communication.
- ECC (Elliptic Curve Cryptography): ECC is an asymmetric encryption algorithm that provides strong security with shorter key lengths compared to traditional algorithms like RSA. It is particularly valuable in resource-constrained environments, such as mobile devices.
- SHA-2 (Secure Hash Algorithm 2): While not an encryption algorithm per se, SHA-2 is a family of cryptographic hash functions widely used for integrity verification and digital signatures. It includes hash functions such as SHA-256 and SHA-3, providing varying levels of security.
- Post-Quantum Cryptography (PQC) Algorithms: As the field of quantum computing advances, there is ongoing research and development of encryption algorithms that are resistant to attacks by quantum computers. Examples include lattice-based cryptography, hash-based cryptography, and code-based cryptography.
What Are the Benefits of Encryption?
Encryption provides several important benefits in the realm of information security, privacy, and data protection.
Data Protection
As the volume of data being created, managed and stored by organizations around the world increases and diversifies, it becomes ever more important to have a data protection plan in place. Breaches and cyberattacks are on the rise, and can often result in some severe consequences for businesses of all sizes. These include revenue loss, damage to brand reputation, loss of trust from customers, operational disruptions, and even legal ramifications. According to a report from IBM and the Ponemon Institute, in 2023, the average cost of a breach was $4.45 million, which is a substantial financial burden for a business to take on. There are a number of techniques that can be used to protect and secure data from a breach, but the most effective method is encryption. Having an encryption solution in place ensures that sensitive information is kept private and gives businesses peace of mind, knowing that their data is always protected.
Communication Security and Privacy
Encryption safeguards communication channels, ensuring that the content of messages or data is secure and private. This is particularly crucial in the age of online communication and electronic transactions. The choice of encryption algorithm often depends on the specific use case, security requirements, and industry standards.
Secure Authentication
Encryption plays a role in secure authentication processes. Digital signatures and certificates often rely on encryption to verify the authenticity of messages, documents, or individuals.
Risk Mitigation
In the event of a security breach or data theft, encrypted data poses a significantly higher barrier to unauthorized access. Even if an attacker gains access to the encrypted data, they would still need the encryption key to make sense of the information.
Compliance
One of the biggest factors influencing organizations to implement encryption within their IT environments is compliance. There are major regulations that exist across several specific sectors, with the purpose of maintaining the security of clients’ personal, and often sensitive, information. Examples include: healthcare (HIPAA), financial services (PCI-DSS and GLBA), biotechnology (FDA) and the energy industry, and IoT (NERC and FERC). Failure to comply with these regulations can result in a number of penalties, including fines, increased fees, and revocation of rights to interact with clients in given industries. Encryption provides that level of protection a business needs to ensure sensitive data won’t be compromised, and confirms that the necessary precautions have been taken to keep data safe.






Customer Trust
According to a study by Security.org, one in four Americans won’t do business with data-breached companies (ZDNet). One of the biggest and most significant consequences of a data breach, is the impact it has on customer trust and loyalty. For example, between 2013 and 2014, Yahoo! experienced the largest data breaches of all time, impacting 3 billion user accounts. After announcing the breaches publicly, Yahoo was forced to reduce its sale price to Verizon by $350 million, pay an $80 million settlement in 2018, and later a further $35 million fine. In the years that followed, they were surpassed by several other search engines and email service providers, who exercised better security practices. Implementing data protection, such as encryption, enables businesses to build trust with their customers and ensure that their sensitive information won’t be compromised in the event of a breach.
Encryption is a fundamental tool for ensuring the confidentiality, integrity, and privacy of sensitive information, playing a crucial role in protecting data in various contexts, from personal communications to business operations.
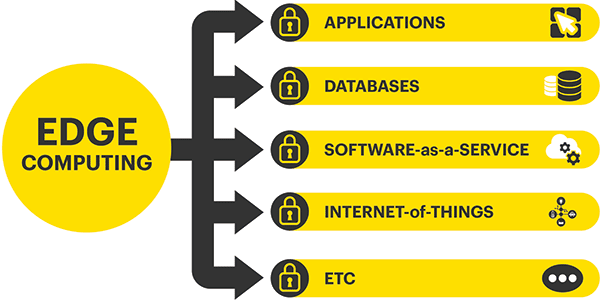
Encryption and Edge Computing
Edge computing organizations face some unique challenges when it comes to data security. Businesses with hundreds to thousands of IoT devices, for example, are at risk because they often manage and store users’ personal data and don’t have built-in data protection. A retail chain may have many different locations, each holding mass amounts of sensitive information, and a remote office or manufacturing warehouse may not be physically secure. A smart city could be completely taken out, (including power systems, streetlights, and traffic management systems) if they fall victim to a breach.
Edge computing environments are often more susceptible to breaches, because they aren’t physically secure, and often store sensitive information that needs to be kept private. It is for these reasons that edge computing sites can benefit from implementing encryption. Encryption provides an additional layer of protection for these environments, to keep their data from being compromised or stolen. It also helps edge organizations across different industries remain compliant, in order to abide by specific data protection regulations.
Learn more about what defines an ‘edge” environment, in our Beginners Guide to Edge Computing.
Additional Encryption resources you may find helpful:
StorMagic SvSAN and Encryption
Available as an additional feature on top of the base SvSAN license, SvSAN’s data encryption feature is the most cost-effective encryption solution for storing data in edge computing environments. The 100% software approach eliminates the need for operating system or hypervisor-level encryption and does not require any special hardware. You get a simple and inexpensive way to protect sensitive data at the edge, where servers aren’t typically setup in a secure location.
SvSAN’s data encryption feature delivers ultra-secure encryption using a FIPS 140-2 compliant encryption algorithm (XTS-AES-256) and meets HIPAA, PCI DSS and SOX requirements. It does not require special self-encrypting disk drives, RAID cards or FPGA/ASICs and has the flexibility to encrypt all mirrored data, or just selected volumes. The data is encrypted in-flight, before it is written to disk.
SvSAN’s data encryption feature has been developed with the flexibility to work with any KMIP-compliant key manager, including StorMagic SvKMS. Visit the SvSAN Data Encryption page to learn more.
StorMagic SvKMS and Encryption
StorMagic SvKMS enables secure and effective encryption key management when using SvSAN’s data encryption feature. It is a powerful encryption key management solution that allows organizations to store keys locally, in the datacenter, or cloud. It adapts to any environment and integrates with any existing encryption workflow, to deliver flexible, robust, simple key management, all within a single platform, at a surprisingly low cost.
SvKMS eliminates the need for hardware security modules (HSMs) and uses a REST API for easy integrations into any workflow with custom key imports facilitating an easy transition from legacy solutions. It is FIPS 140-2 certified, allows advanced identification and access management through SAML 2.0, and can be configured as a single- or multi-tenanted solution.
SvKMS is a separately licensed product to SvSAN and the two can be used independently of each other. Furthermore, if your organization is already using an existing KMS solution, providing it is KMIP-compliant, SvSAN’s data encryption feature is already fully compatible and can be integrated with it immediately.