What is BYOK?
Many data security professionals believe that encryption is the best technology for securing data against breaches. However, organizations that decide to move their data to the cloud are often faced with a dilemma when it comes to encryption; their cloud service provider (CSP) maintains access to their encryption keys, and ultimately, their data. For highly regulated industries and organizations storing sensitive data, this can be unsettling and even against compliance regulations.
Bring Your Own Key (BYOK), also referred to as Customer Supplied Encryption Keys (CSEK), is a model of encryption key management that enables customers to take full control of their encryption keys when storing data in the cloud. It allows them to use their own encryption key management software to store their encrypted keys outside of the cloud, instead of in the cloud, alongside their data. It enables the separation of lock (i.e. the encryption that the CSP provides) and key (i.e. the digital encryption key you want to store locally). This separation of lock and key is considered best practice when it comes to securing data via encryption.
How Does BYOK Work?
While there are many benefits to storing data in the cloud, one of the main concerns for organizations is security; once their data is in the cloud, it’s no longer in their control. Data stored in the cloud physically resides with the cloud service provider (CSP), rather than with the business that it belongs to.
The concept of BYOK allows an organization to retain control of the keys to their encrypted data, entirely separate from the cloud provider(s) they use to store their data. In order to achieve this, the organization must use a third party to generate keys that encrypt the data encryption keys (DEKs) produced by the CSP’s own key manager. A key generated by a third party and used to encrypt a CSP’s DEK is known as a key encryption key (KEK).
The KEK ‘wraps’ the DEK, ensuring that only the organization, which retains control and ownership of the KEK, can decrypt the DEK, and therefore access the data stored within the CSP. This procedure is sometimes referred to as ‘key wrapping’.
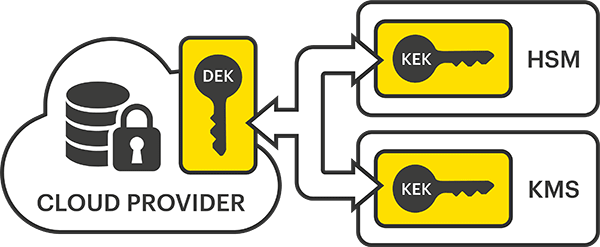
The organization generally has two options when considering a third party to generate KEKs and provide the key wrapping. Firstly hardware security modules (HSMs) – dedicated pieces of hardware that are very secure but also expensive, and may require further technology to allow them to connect to the cloud. The second option is to use a software-based key management system (KMS) installed on regular servers. The benefits of using a software-based KMS are it’s greater flexibility, easier management, and generally lower cost.
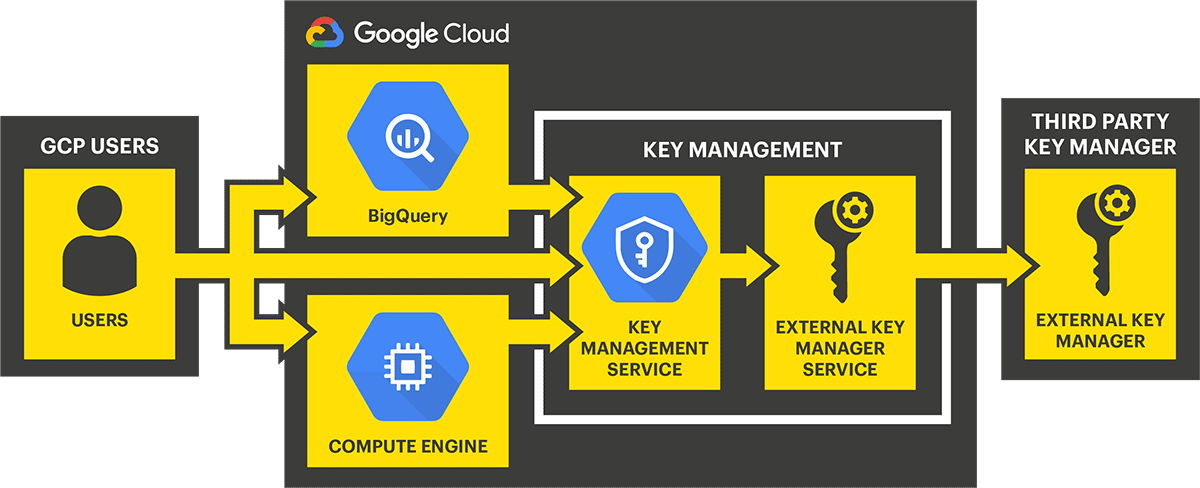
CSPs are beginning to understand and act on the concern around having key materials reside in the cloud. Addressing this concern has involved adding additional external layers to BYOK schemes to provide key management within the CSP’s interface without the CSP ever storing or controlling the keys themselves. An example of this is the Google Cloud External Key Management (EKM) Program. This program allows users to manage access to their externally managed keys, whether the data they protect resides in the cloud or on-prem.
What Are the Benefits of BYOK?
Implementing a BYOK model of encryption key management delivers several benefits to organizations, including:
Control
One of the main concerns for organizations storing data in the cloud is security; once their data is in the cloud, it’s no longer in their control. BYOK enables organizations to reclaim control of their data. It allows for the separation of lock and key, by giving the business the ability to use their own encryption key management software to store their encrypted keys outside of the cloud. This provides organizations with peace of mind, knowing that they are the only ones that can access their sensitive data. It also gives them the ability to revoke encryption keys from certain people and processes that should no longer have access.
Ease of Management
Managing hundreds to thousands of encryption keys across multiple different platforms (i.e. datacenter, cloud, multi-cloud) can be complex and overwhelming. By implementing a BYOK encryption model, organizations are able to manage all of their encryption keys from a single platform. It centralizes key management, by providing a unified interface for creating, rotating, and archiving encryption keys. If they have data located within different clouds (i.e. multi-cloud), they’re able to consolidate management of those clouds to one key manager.
Compliance
When an organization stores its data and encryption keys in the cloud, they aren’t able to manage their keys as they’d like to — that responsibility falls onto the CSP. Many businesses across different industries are required to adhere to specific regulations when it comes to managing their encryption keys. They have to set up control policies, like key rotation and expiry. When their data and encryption resides in the cloud, it makes it more difficult to keep up on key lifecycle management. They have to rely on the CSPs to keep up with compliance guidelines around key management.
StorMagic SvKMS and BYOK
SvKMS is an encryption key management solution that adapts to any environment. It provides organizations with a single platform to manage all of their encryption keys, anywhere. Whether at the edge, datacenter, cloud or multi-cloud, SvKMS delivers enterprise-grade key management features to any encryption workflow.
With SvKMS, organizations can enable BYOK, and control their encryption keys from a single platform-agnostic environment outside of the cloud. SvKMS’s BYOK feature provides organizations with more comprehensive key lifecycle management than they’d receive through their CSP, and allows them to deploy specific applications not tied to the CSP’s architecture. Learn more about what SvKMS can do with BYOK on the feature page.
SvKMS integrates with several different cloud-based platforms and applications, including Microsoft Azure, AWS, Salesforce, OpenStack, and Google Cloud. Visit our integrations page to learn more about the different cloud platforms that SvKMS integrates with.





