The concept of Trusted Computing is to develop and promote technologies for protection from threats posed by malicious entities, without infringing on the rights of end users. This is achieved through hardware enhancements and associated software modifications.
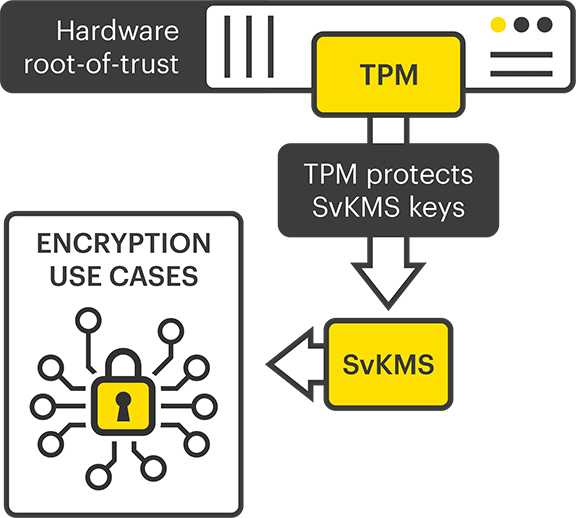 StorMagic is working towards this objective by ensuring our SvKMS software embraces and is compatible with the agreed standards for Trusted Computing. The first of these developments is ensuring SvKMS is compatible with trusted platform modules (TPMs)
StorMagic is working towards this objective by ensuring our SvKMS software embraces and is compatible with the agreed standards for Trusted Computing. The first of these developments is ensuring SvKMS is compatible with trusted platform modules (TPMs)
Trusted Platform Modules provide advanced data security
The TPM specification is one that has been established by the Trusted Computing Group (TCG). StorMagic SvKMS provides root-of-trust encryption key protection by supporting the Trusted Platform Module 2.0 standard. The TPM acts as the root-of-trust, where a standard Key Encryption Key (KEK) is wrapped within a Data Encryption Key (DEK). The DEK is then stored within the TPM and key protection functionality is controlled within the SvKMS user interface.
By using TPMs, organizations can trust that their data is safe because their keys are protected from within a trusted environment – the TPM itself. When a user wants to encrypt or decrypt a piece of information the data is protected by the TPM root key through a chain of key wrapping.
What is a Trusted Platform Module?
A TPM chip is a secure crypto-processor designed specifically to carry out cryptographic operations directly inside the CPU. TPMs are found in most servers, and as a hardware root-of-trust, they have distinct advantages and can be made robust against attacks, as well as tamper resistant. Combining software and hardware together can protect root secrets better than software alone, therefore the TPM support included with StorMagic SvKMS ensures organizations can safely implement a Trusted Computing strategy and keep data-in-use secure.